This post is based on differnet articles from www.ssh.com.
The motivation for using public key authentication for ssh-Login over simple passwords is security. Public key authentication provides cryptographic strength that even extremely long passwords cannot.
SSH Keys and Public Key Authentication
The SSH protocol uses public key cryptography for authenticating hosts and users. The authentication keys, called SSH keys, are created using the keygen program. SSH introduced public key authentication as a more secure alternative to the older .rhosts authentication.
It improved security by avoiding the need to have password stored in files, and eliminated the possibility of a compromised server stealing the user’s
password.
However, SSH keys are authentication credentials just like passwords. Thus, they must be managed somewhat analogously to user names and passwords. They should have a proper termination process so that keys are removed when no longer needed.
Key Pair – Public and Private
In the SSH public key authentication use case, it is rather typical that the users create (i.e. provision) the key pair for themselves. SSH implementations include easily usable utilities for this (for more information see ssh-keygen and ssh-copy-id).
Each SSH key pair includes two keys:
- A public key that is copied to the SSH server(s). Anyone with a copy of the public key can encrypt data which can then only be read by the person who holds the corresponding private key. Once an SSH server receives a public key from a user and considers the key trustworthy, the server marks the key as authorized in its authorized_keys file. Such keys are called authorized
keys.
- A private key that remains (only) with the user. The possession of this key is proof of the user’s identity. Only a user in possession of a private key that
corresponds to the public key at the server will be able to authenticate
successfully. The private keys need to be stored and handled carefully, and no copies of the private key should be distributed. The private keys used for user authentication are called identity keys.
What Is ssh-keygen?
This document is about OpenSSH version of`ssh-keygen`. If you wish to generate keys for PuTTY, see PuTTYgen on Windows or PuTTYgen on Linux. Ssh-keygen is a tool for creating new authentication key pairs for SSH. Such key pairs are used for automating logins, single sign-on, and for authenticating hosts.
Creating an SSH Key Pair for User Authentication
The simplest way to generate a key pair is to run ssh-keygen without arguments. In this case, it will prompt for the file in which to store keys. Here’s an example:
box01:~$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/userfoo/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/userfoo/.ssh/id_rsa.
Your public key has been saved in /home/userfoo/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:Up6KjbnEV4HgdljsaljdsalM393QdQsK3Z0aTNBz0DoirrW+c userfoo@box01
The key’s randomart image is:
+—[RSA 2048]—-+
| . ..oo..|
| . . . . .o.X.|
| . . o. ..+ B|
| @.B… . |
| o.=. o. . . .|
| .oo E. . .. |
+—-[SHA256]—–+
box01:~$
First, the tool asked where to save the file. SSH keys for user authentication are usually stored in the user’s .ssh directory under the home directory. However, in enterprise environments, the location is often different. The default key file name depends on the algorithm, in this case id_rsa when using the default RSA algorithm. It could also be, for example, id_dsa or id_ecdsa.
Then it asks to enter a passphrase. The passphrase is used for encrypting the key, so that it cannot be used even if someone obtains the private key file. The passphrase should be cryptographically strong.
SSH supports several public key algorithms for authentication keys. These include:
- rsa – an old algorithm based on the difficulty of factoring large numbers. A key size of at least 2048 bits is recommended for RSA; 4096 bits is better. RSA is getting old and significant advances are being made in factoring. Choosing a different algorithm may be advisable. It is quite possible the RSA algorithm will become practically breakable in the foreseeable future. All SSH clients support this algorithm.
- dsa – an old US government Digital Signature Algorithm. DSA in its original form is no longer recommended.
- ecdsa – a new Digital Signature Algorithm standardized by the US government, using elliptic curves. Most SSH clients now support this algorithm.
- ed25519 – this is a new algorithm added in OpenSSH. Support for it in clients is not yet universal. Thus its use in general purpose applications
may not yet be advisable.
The algorithm is selected using the -t option and key size using the -b option. The following commands illustrate:
ssh-keygen
-t rsa -b 4096
ssh-keygen -t dsa
ssh-keygen
-t ecdsa -b 521
ssh-keygen -t ed25519
Normally, the tool prompts for the file in which to store the key. However, it can also be specified on the command line using the -f <filename> option.
ssh-keygen -f ~/mykey-key-ecdsa -t ecdsa -b 521
Copying the Public Key to the Server
To use public key authentication, the public key must be copied to a server and installed in an authorized_keys file. This can be conveniently done using the ssh-copy-id tool. Like this:
ssh-copy-id -i ~/.ssh/id_rsa.pub user@host
Once the public key has been configured on the server, the server will allow any connecting user that has the private key to log in. During the login process, the client proves possession of the private key by digitally signing the key exchange.
Location of the Authorized Keys File
With OpenSSH, the authorized keys are by default configured in .ssh/authorized_keys in the user’s home directory. The AuthorizedKeysFile configuration option in /etc/ssh/sshd_config specifies where the SSH server looks for authorized keys. The option may contain more than one location, separated by spaces. %% is replaced by literal %, %h by the home directory of the user being authenticated, and %u by the login name of the user. For example, /var/ssh/%u/ak would cause the SSH server to look for authorized keys for the user james from /var/ssh/james/ak.
Format of the Authorized Keys File
In OpenSSH, a user’s authorized keys file lists keys that are authorized for authenticating as that user, one per line. Lines starting with # and empty lines are ignored.
Each line contains a public SSH key. The public key may be preceded by options that control what can be done with the key. The all options supported see the man pages.
How To Use Putty with an SSH Private Key Generated by OpenSSH
Putty cannot use key-files generated by ssh-keygen. If you try to use such a file you will get the following error:
Unable to use key file “C:\Keys\id_rsa” (OpenSSH SSH-2 private key)
You have to convert ssh-keygen generated keys to a Putty readable format.
For this conversion you can use the Putty Key Generator (puttygen). Start puttygen, and click on Conversions->Import key, then click Browse and select the private key generated with openssh (e.g. id_rsa).
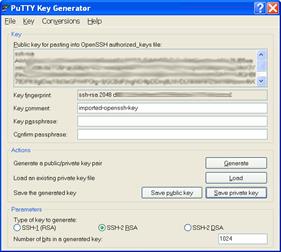
Then simply save the converted private key under a meaningful new name (e.g. id_rsa_putty.ppk). Now you can start Putty, enter the machine IP address as usual and then go to Connection->SSH->Auth.
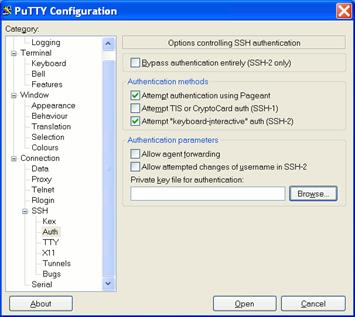
Click Browse, and select your just created private key file (e.g. id_rsa_putty.ppk), go back to Session and save the session.


